A Complete Guide to Connect Google Cloud/ G Suite Connector with Microsoft Entra ID
- The Tech Platform

- Apr 24, 2024
- 5 min read
This article is a complete guide that provides detailed instructions to integrate Google Cloud with Microsoft Entra ID. It covers the prerequisites for the integration, a step-by-step guide on the process, the benefits of the integration, and important security considerations. The article concludes with a summary and final thoughts on the importance and benefits of integration.
Connecting Google Cloud with Microsoft Entra ID
Connecting Google Cloud with Microsoft Entra ID is a process that involves integrating the two platforms to enable seamless identity management and single sign-on (SSO). This integration allows organizations to manage user access to Google Cloud resources using Microsoft Entra ID, enhancing security and simplifying the user experience.
What is Single Sign-On (SSO)?
Single Sign-On (SSO) is an authentication scheme that allows users to log in with a single ID and password to several independent software systems. With SSO, only once a user needs to enter their login credentials (username, password, etc.) on a single page to access all their SaaS applications.
A step-by-step guide to Connect Google Cloud/ G Suite Connector with Microsoft Entra ID
To get started, you need the following items:
A Microsoft Entra subscription.
Google Cloud / G Suite Connector by Microsoft single sign-on (SSO) enabled subscription.
A Google Apps subscription or Google Cloud Platform subscription.
STEP 1: Add Google Cloud / G Suite Connector by Microsoft from the gallery
1. Sign in to Microsoft Entra Admin Center. In the left panel, navigate to "Identity => Applications => Enterprise applications".

2. Click on "+ New application".

3. Type "Google Cloud/G Suite connector by Microsoft" in the search box.

4. Select "Google Cloud/G Suite connector by Microsoft" from the result.
5. Enter the name. For example, I have used the "Integration with Google Cloud" (based on the article topic).
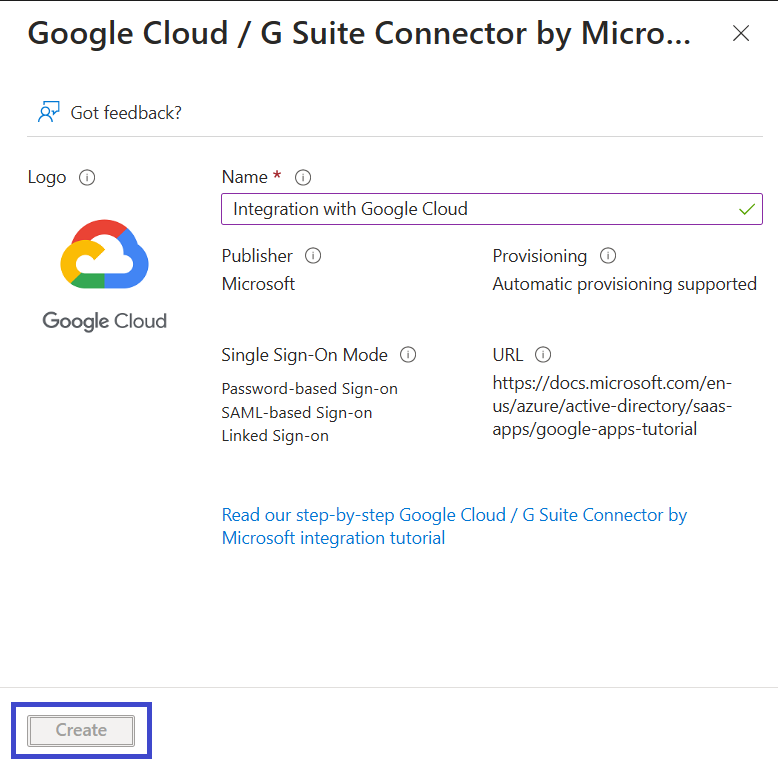
6. Click Create. Your Google Cloud app will be added.
STEP 2: Configure Microsoft Entra SSO for Google Cloud / G Suite Connector
1. Navigate to "Identity => Applications => Enterprise application => Integration with Google Cloud (name of Google Cloud/G Suite connector by Microsoft)".
2. In the left panel, click "Single sign-on". Select "SAML".

3. Under the "Basic SAML Configuration" section, click "Edit".

4. Enter the following information to configure for the Gmail:
Identifier (any one of the following)
google.com/a/yourdomain.com
google.com
https://google.com
https://google.com/a/yourdomain.com
Reply URL (any one of the following)
https://www.google.com
https://www.google.com/a/yourdomain.com

If you want to configure the Google Cloud platform, then enter the following information
Identifier
google.com/a/yourdomain.com
google.com
https://google.com
https://google.com/a/yourdomain.com
Reply URL
https://www.google.com/acs
https://www.google.com/a/yourdomain.com/acs
5. Enter the following URL in the Sign on the URL box

Click Save.

6. Your Google Cloud / G Suite Connector by Microsoft application expects the SAML assertions in a specific format, which requires you to add custom attribute mappings to your SAML token attributes configuration. The following screenshot shows an example for this. The default value of Unique User Identifier is user.userprincipalname but Google Cloud / G Suite Connector by Microsoft expects this to be mapped with the user's email address. For that you can use user.mail attribute from the list or use the appropriate attribute value based on your organization configuration.

7. In the SAML Certificate section, click on "Download" to download the "Certificate (Base64)".

8. Scroll down to the "Set up Integration with Google Cloud" section. Copy the URL as per your requirements.

STEP 3: Create Microsoft Entra Test User
1. Navigate the "Identity => Users => All Users".

2. Click "+ New user => Create new user" .
3. Enter the following information
Display Name - Manpreet Singh
User principal name - manpreetsingh@microsoft.com
Create a password
4. Click "Review + create" and click "Create".
STEP 4: Assign Microsoft Entra Test User
1. Navigate to "Identity => Applications => Enterprise applications => Integration with Google Cloud (As per Google Cloud / G Suite Connector Name)".
2. In the left panel, click "User and groups". Click "Add user/groups".

3. Select Manpreet Singh from the list. Select a role from the dropdown menu list to assign a particular role.
Or you can add the user as per your requirements

Click Select.
4. Click "Assign".

STEP 5: Configure Google Cloud / G Suite Connector By Microsoft SSO
1. Sign in to Google Cloud / G Suite Connector by Microsoft Admin Console.
2. Navigate to "Menu => Security => Authentication => SSI with Third-party IdP".

3. Enter the following information to configure the Third-party SSO profile for your organization:
Sign-in page URL (Copy the Login URL from the "Set up Integration with Google Cloud" section in STEP 2 (8))
Sign-out page URL (Copy the Logout URL from the "Set up Integration with Google Cloud" section in STEP 2 (8))
Verification certificate (Add downloaded (Certificate (Base64))
Check the "Use a domain specific issuer"
Add change password URL - https://account.activedirectory.windowsazure.com/changepassword.aspx


4. Click Save.
STEP 6: Test SSO
Navigate to "Google Cloud / G Suite connector => Single sign-on". Scroll down and click on "Test" to test this application.

Benefits of the Integration
Connecting Google Cloud with Microsoft Entra brings several advantages:
Automated Identity Management: Linking user identities between Google Cloud and your current identity system means you can automate keeping Google identities up-to-date and connected to existing Microsoft Entra users.
Access Control: In Microsoft Entra, you can manage who can access Google Cloud / G Suite Connector.
Single Sign-On: Users can automatically sign in to Google Cloud / G Suite Connector using their Microsoft Entra accounts. This removes the need to sync passwords to Google Cloud and ensures that any security rules or extra verification steps to set up in Microsoft Entra are followed.
Centralized Account Management: All accounts can be managed from one central location.
Security Consideration while connecting Google Cloud with Microsoft Entra ID
When you connect Google Cloud with Microsoft Entra, there are some important security things to think about:
Identity Federation: Linking user identities between Google Cloud and your current identity management system. By doing this, you can automatically update Google identities based on existing users in Microsoft Entra. This helps reduce the chance of unauthorized access to old or unused accounts.
Authentication: Depending on how you've set up Microsoft Entra ID, it might handle authentication by itself, use pass-through authentication, synchronize passwords, or let an on-premises AD FS server handle it. This makes sure that any security rules or extra verification steps (like using multiple factors to confirm identity) you've set up are followed.
Provisioning: Changes made in Microsoft Entra ID are copied to Google Cloud, but changes made in Google Cloud are not copied to Microsoft Entra ID. Also, passwords aren't included in this process. This helps keep your security strong by quickly updating who has access to what on both platforms.
Least Privilege Access: It is important to permit the user to do their jobs. This limits the damage if someone's account is compromised. This rule applies to cloud services such as Azure, Amazon Web Services, and Google Cloud.
Secure Hybrid Access (SHA): Use SHA to safeguard your older authentication systems, whether on-premises or in the cloud. This involves linking them up with Microsoft Entra ID for extra protection.
Conclusion
Integrating Google Cloud with Microsoft Entra ID is a strategic move that can enhance security, improve user experience, and drive operational efficiency. It’s an important topic for IT administrators, security professionals, and decision-makers leveraging or considering leveraging cloud services in their organizations.




Comments