Set Up IAM User And Alert For Budget In AWS
- The Tech Platform

- Feb 6, 2021
- 5 min read
AWS Identity and Access Management (IAM) is one of the AWS services that helps you securely control AWS resources. Any organization has different resources for different services, so IAM controls who is authenticated and authorized (permission) to use these resources. When you first start on AWS, you begin with a single sign-in identity who has complete access to all AWS services and resources. This identity is called the AWS root user and can be accessed via the credentials you used while creating the AWS account.
After creating the AWS root account, the next step is to start working with the services of AWS. Before this, it is strongly recommended that you do not use the AWS root account even for Administrative tasks. To begin, for any further services use an IAM user and only use the root account to create an IAM user.
IAM Features
Granular Permissions
You can grant different permissions to different people for different resources.
E.g., you allow a user complete access to Amazon EC2, Amazon S3, and dynamo DB for other users you allow only read access to amazon EC2 only nothing else so these users access resources according to their permissions.
Secure access to AWS resource
IAM credentials provide secure access for your application to access other AWS resources
eg. S3 buckets, dynamo DB
Multi-factor Authentication (MFA)
You can add multi-factor authentication to your account for extra security
E.g., along with a password, you additionally provide a code from a configured device.
IAM main resources
IAM users
IAM groups
IAM roles
IAM policies
IAM users are usually a physical person like you or me. It usually represents a person or service who uses it to interact with AWS
Now users can be grouped together IAM Groups which use to specify permissions for a collection of users, suppose you have a group called admins, and give that types of permissions that administrators typically need. any user in that group automatically has the permissions that are assigned to the group now if a new user joins organizations and should have administrator privilege you can assign these permissions by adding the user to that group.
IAM roles are only for internal usage within the AWS resources or services, these are very similar to a user, roles are given to machines and the user is going to be a physical person.
IAM Policies are written in JSON documents, which defines what each of the above can and cannot do.
Create an IAM user
Step 1
Login to AWS management console with root user credentials.
Step 2
Search IAM on find services search bar on the management console dashboard.
IAM is a global service, IAM users not specific to availability zone its AWS global
Step 3
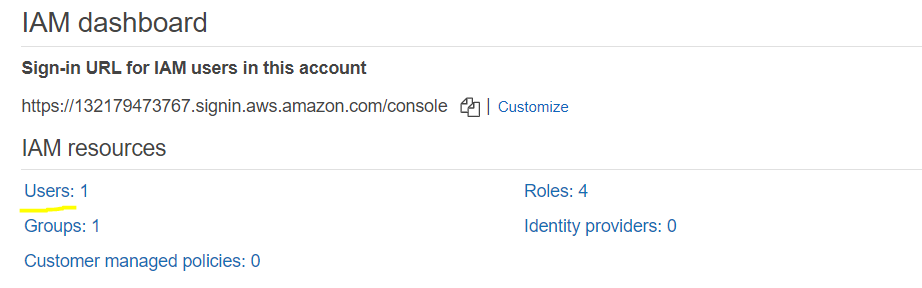
Now we have an IAM dashboard where we need to click on users.
Step 4
Then click on add user and a screen is open to add a new user and fill the respective details like below where we give both programmatic access and AWS management console access with an autogenerate password and then click on Next: permissions
Step 5
Now we can set permissions in three ways:
Add user to the group - Add user to an existing group where the new user will get the same permissions to define in the new group
Copy permissions from existing users - as the name suggests you will get the same permissions from the copy user.
Attach existing policies directly - you can define the policies directly from here
Here, I'm attaching existing policies directly and later add the user to the group so that you can familiar with both options.so when you click this option you will get many options listed that are already grouped together according to their services here I'm selecting administrator access so this user will get all the administrator rights.
Step 6
Click on Next: Tag here you can add key-value pairs to the user I'm adding one tag here
Step 7
Click on Review and create a user and new window where you have the detail of newly created user download a CSV file which includes an auto-generated password
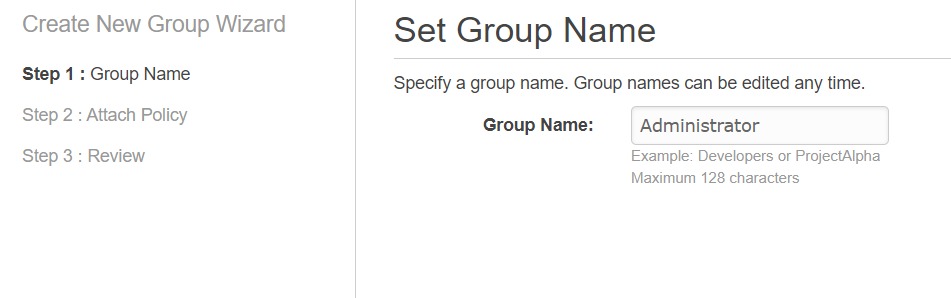
Step 8
Now, close this window and click on groups and click on add new group and give a group name, lets say, administrator.
Step 9
In the next step, we need to attach policies earlier we set the policy to one user now we attach the administrator access to the group, you can use the filter also to look out for other policies
Step 10
Now, click on review and create group, now you have a list of created group and click on the checkbox to the newly created group and click on Group actions and click add users to a group where you have a list of created users, select the user and click on add users.
Step 11
Now, we add the user to the administrator group. We need to detach the existing policies so that the user inherits the group policies. Go to users and select the user; there we have a permission tab. We have to remove the attached directly policies. As you can see, the policy is already attached from the group tab.
Step 12
Now, log in to the newly created IAM user and go to the IAM user dashboard. At the top, you see a sign-in URL for IAM users. Click on this URL and a new login window will open.
Step 13
Enter your username and password from the CSV file, on the first login, you need to change the password, as this is an auto-generated password.
Here, you can see a new dashboard with administrative rights on an IAM user account.
Now we set the budget so that our AWS bill does not cross our budget.
For this, we need to back to the root user account. Logout from this IAM user and login with the root user account Step 14
Go to My billing dashboard, click on budgets, and create a budget. Select the budget type as the cost budget.
Step 15
Click on set your budget and enter budget details including your budgeted amount. Here, I give my budget $1 and in the next section, we set the alert so that when it consumes the budget, we get an alert for this.
Step 16
Leave the rest of the fields as default and click on set alerts and set the alert threshold after how much % of the budget you want alert and give the email contact where you get the alert. Also, you can set alerts based on actual cost or forecasted costs.
Click on confirm budget review and create, you will get a list of budgets created and click on the budget created you will get a dashboard which shows the budget details graphically.
That's it. You set your monthly budget and got the alarm before the bill goes beyond your budget. So this is how you create IAM users, add the user to the group, and assign the policies only where the user needs to be authorized and set a monthly budget and alerts in AWS. I hope you enjoyed this article! Please comment if you have any queries.
Source: C# Corner
The Tech platform
































Comments